On this page...
What Does Suspicious Activity Look Like?
Suspicious activity is any observed behavior that could point to terrorism or terrorism-related crime. The "If You See Something, Say Something®" campaign respects citizens' privacy, civil rights, and civil liberties by emphasizing behavior, rather than appearance, in identifying suspicious behavior. Factors such as race, ethnicity, and/or religious affiliation are not suspicious. Some activities could be innocent, but trained law enforcement officials can determine whether the behavior warrants further action.
Whether you are on your way to work, shopping at a store, or traveling on vacation, remember: We all play a role in keeping our communities safe. Remember to stay alert and say something when you see something suspicious. The below activities should only be reported if they cause suspicion of terrorism.
Back to topSigns of Suspicious Activity
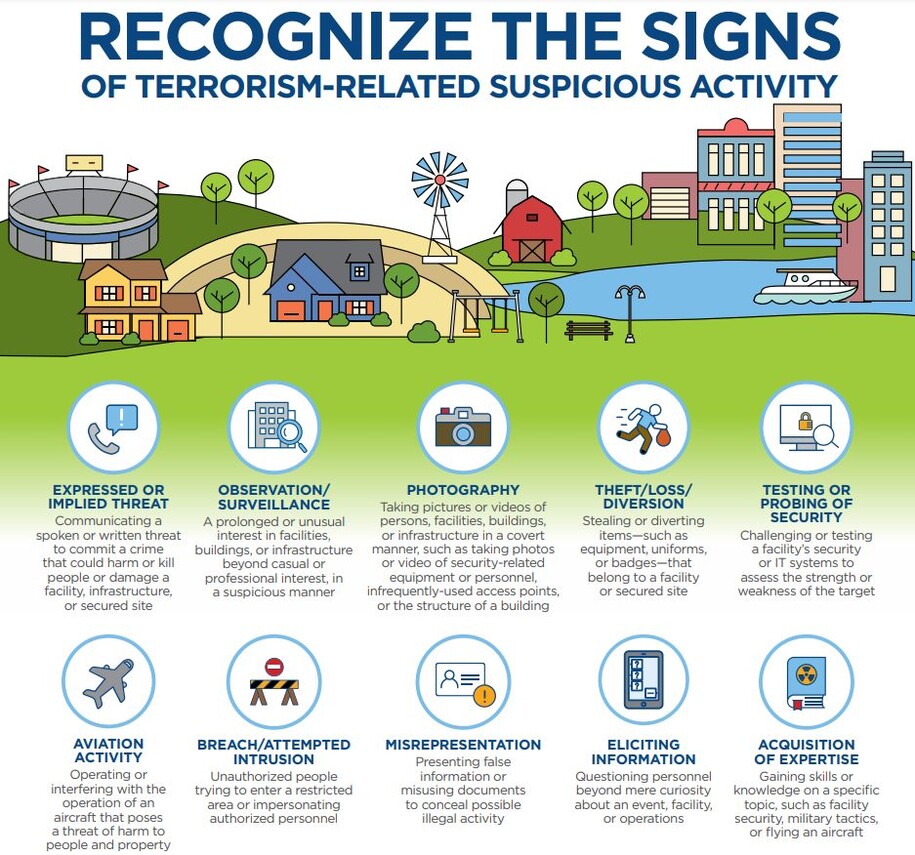
Download the Recognize the Signs Infographic in English or in Spanish.
Recognize the Signs of Suspicious Activity
- Expressed or Implied Threat - Communicating a spoken or written threat to commit a crime that could harm or kill people or damage a facility, infrastructure, or secured site.
- Observation / Surveillance - A prolonged or unusual interest in facilities, buildings, or infrastructure beyond casual or professional interest.
- Photography - Taking pictures or videos of persons, facilities, buildings, or infrastructure in a covert manner, such as photos or video of security related equipment or personnel, infrequently used access points, or structure of a building.
- Theft / Loss / Diversion - Stealing or diverting items—such as equipment, uniforms, or badges—that belong to a facility or secured site.
- Testing or Probing of Security - Challenging or testing a facility's security or IT systems to assess the strength or weakness of the target.
- Aviation Activity - Operating or interfering with the operation of an aircraft that poses a threat of harm to people and property.
- Breach / Attempted Intrusion - Unauthorized people trying to enter a restricted area or impersonating authorized personnel.
- Misrepresentation - Presenting false information or misusing documents to conceal possible illegal activity.
- Eliciting Information - Questioning personnel beyond mere curiosity about an event, facility, or operations.
- Acquisition of Expertise - Gaining skills or knowledge on a specific topic, such as facility security, military tactics, or flying an aircraft.
- Cyberattack - Disrupting or compromising an organization’s information technology systems.
- Recruiting / Financing - Funding suspicious or criminal activity or recruiting people to participate in criminal or terrorist activity.
- Sabotage / Tampering / Vandalism - Damaging or destroying part of a facility, infrastructure, or secured site.
- Materials Acquisition / Storage - Acquisition and/or storage of unusual materials such as cell phones, radio controllers, or toxic materials.
- Weapons Collection / Storage - Collection or discovery of unusual amounts of weapons including explosives, chemicals, or other destructive materials.
- Sector-Specific Incident - Actions which raise concern to specific sectors (e.g., power plant) with regard to their personnel, facilities, systems, or functions.
